Spectrum of supply chain vulnerabilities: examples of potential disruptions | Download Scientific Diagram

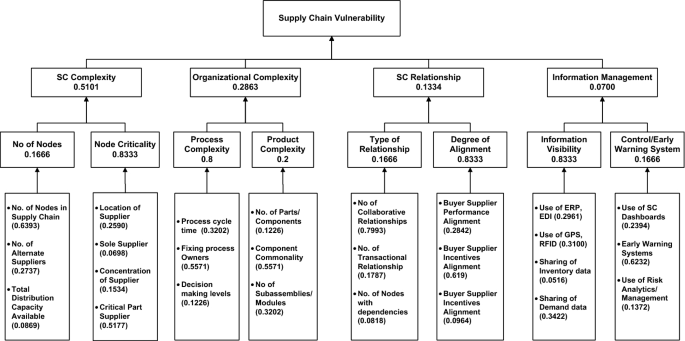
Minimizing the vulnerabilities of supply chain: A new framework for enhancing the resilience | Semantic Scholar

The Supply Chain Vulnerability Scan from Cosmo Tech is now Available on the SAP® Store | Business Wire
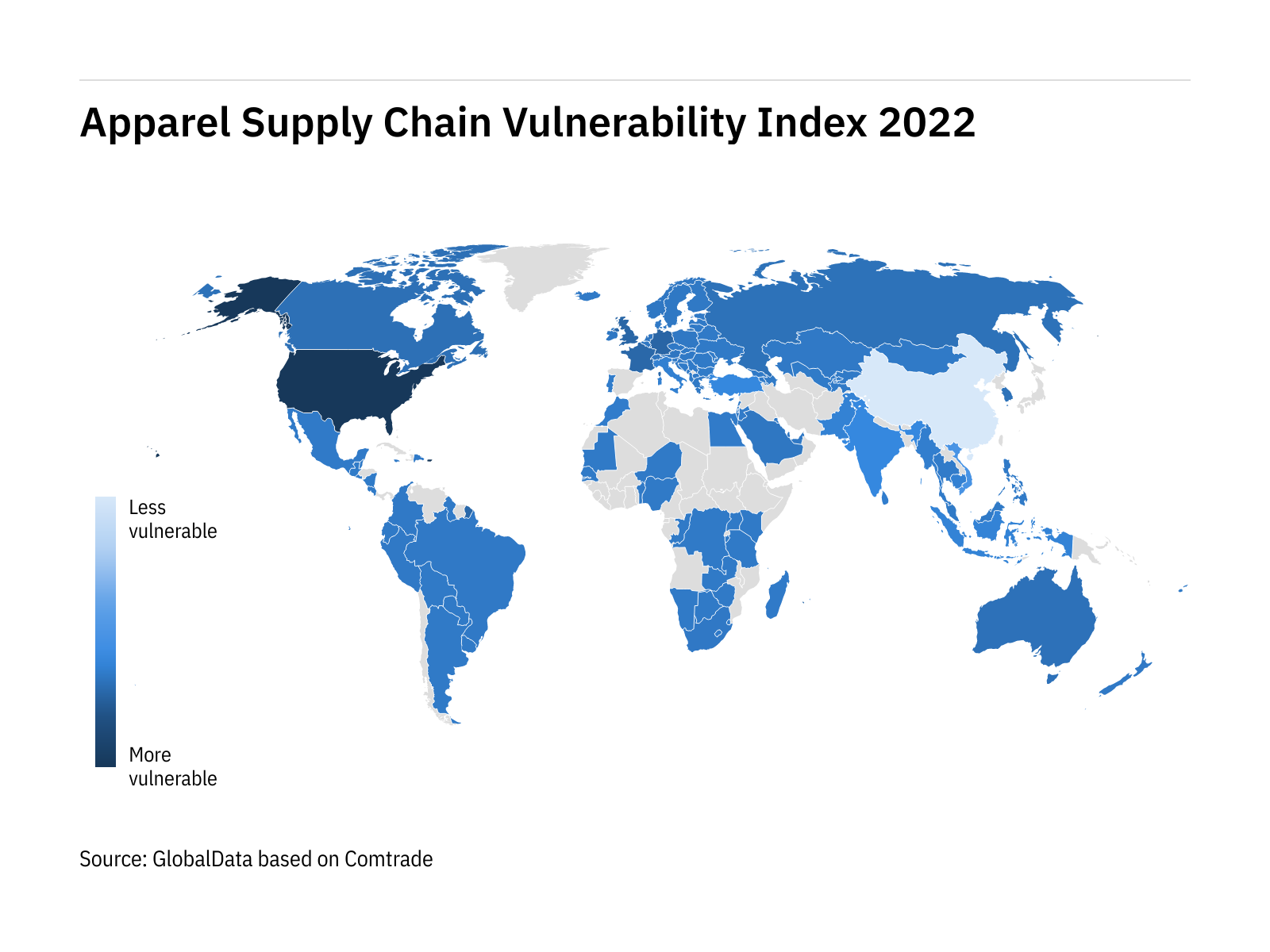
China's resilience shines through in index of world's most vulnerable apparel supply chains - Just Style

PPT - Supply Chain Vulnerability, Risk, Robustness & Resilience PowerPoint Presentation - ID:9092466